Normální zobrazení
-
GamingOnLinux Latest Articles
-
The free game Infinitode 2 - Infinite Tower Defense added Linux support
Here's a fun surprise for you today, Infinitode 2 - Infinite Tower Defense is a free to play game that just added Native Linux support on July 30th.
-
GamingOnLinux Latest Articles
-
Steam Tower Defense Fest 2024 has begun
While I still grumble that Defense is the accepted spelling as a brit I want to always type Defence but anyway the Steam Tower Defense Fest 2024 is now live.
Steam Tower Defense Fest 2024 has begun
-
GamingOnLinux Latest Articles
-
Dome Keeper - A Keeper's Duty is a big free upgrade out now
While developer Bippinbits are working on their next game that has a title so long it's just hilarious (PVKK: Planetenverteidigungskanonenkommandant), they are still updating Dome Keeper with a big free update out now.
Dome Keeper - A Keeper's Duty is a big free upgrade out now
-
Latest

-
Nobody Owes Trump Their Vote. Not Even Kyle Rittenhouse.
Update: About 14 hours after Rittenhouse shared his video explaining his support for Ron Paul, declaring that "you must stand by your principles," he announced that he spoke "with members of the Trump's [sic] team" and that he is now "100% behind Donald Trump." "A lot of people are upset that I said I'm going to be writing in Ron Paul for president of the United States, and that is true. I will be writing in Ron Paul." So said Kyle Rittenhouse in
Nobody Owes Trump Their Vote. Not Even Kyle Rittenhouse.

Update: About 14 hours after Rittenhouse shared his video explaining his support for Ron Paul, declaring that "you must stand by your principles," he announced that he spoke "with members of the Trump's [sic] team" and that he is now "100% behind Donald Trump."
"A lot of people are upset that I said I'm going to be writing in Ron Paul for president of the United States, and that is true. I will be writing in Ron Paul." So said Kyle Rittenhouse in a recent video posted to X. A lot of people, it appears, are indeed upset. Should they be?
Rittenhouse catapulted to national attention in 2020 when, at age 17, he armed himself, traveled to Kenosha, Wisconsin, during a night of riots and civil unrest, and shot three men, killing two. It was always Rittenhouse's contention that he'd acted in self-defense, and his arrest galvanized many in the conservative movement who said the prosecution was motivated not by justice but by the political moment. Supporters helped raise $2 million for Rittenhouse's bail, and he ultimately attracted the attention of former President Donald Trump, who defended him while in office and who hosted Rittenhouse at Mar-a-Lago after leaving the White House.
So one of the primary reactions to Rittenhouse's choice for president is that he's guilty of betrayal. Trump and the MAGA movement had his back when his life took its most dire turn, the thinking goes, so Rittenhouse owes them his loyalty at the ballot box. That general sentiment is summed up aptly by the one-and-only Catturd: "I can stomach a lot of things—but backstabbing millions who supported you at your lowest point. Then turning on Trump right after he got shot," he said in a viral post. "Can't stomach it—won't put up with it—forgotten forever."
In other words, Rittenhouse is allegedly in debt to Trump and his followers for supporting his claims of innocence. He was acquitted in 2021 of all charges, including first-degree reckless homicide, two counts of first-degree recklessly endangering safety, first-degree intentional homicide, and attempted first-degree intentional homicide. That was the right decision. And it was the one the jury came to because that is what the evidence clearly supported. The right to self-defense is not selectively available to people with certain views. Rittenhouse owes no one a thing for not getting convicted of charges that prosecutors should not have brought to begin with.
So why did Trump fail to gain Rittenhouse's support? "Unfortunately, Donald Trump had bad advisers making him bad on the Second Amendment, and that is my issue," he said in his video. "If you cannot be completely uncompromisable on the Second Amendment, I will not vote for you." Trump's record includes a bump stock ban, which Reason's Jacob Sullum noted turned "peaceful gun owners into felons by fiat," and his support for red flag laws. Those moves may not be deal-breakers for many people, including other staunch supporters of the Second Amendment. They apparently are for Rittenhouse. It's his one vote, and he can do with it what he wants.
Yet his announcement also elicited what has become the predictable response, on both the left and the right, to similar defections from the mainstream: You're helping elect the other guy. For one, that vastly overstates the power of a vote—an unpopular thing to say, sure, but true nonetheless. And it's particularly true for Rittenhouse, who lives in the Dallas–Fort Worth area; if he's casting his vote there, I'm going to go out on a limb and assume it will not derail Trump's electoral victory in Texas, which is almost assured.
But even if it were true that Rittenhouse's vote would have some sort of Earth-shattering effect on the outcome of the 2024 election, a vote is earned. It's an expression of support. If neither mainstream option can produce a platform that is sufficiently palatable to someone, they certainly have the prerogative to make that known—by supporting someone else or, gasp, not voting altogether.
After all, no one is entitled to your vote. They're not entitled to it simply because they're a member of a particular political party, and they're not entitled to it for supposedly being less bad than the other side. And they're certainly not entitled to it just because they said supportive things about you in a time of need.
The post Nobody Owes Trump Their Vote. Not Even Kyle Rittenhouse. appeared first on Reason.com.

-
Latest

-
RFK Jr. Pays Lip Service to the Debt While Pushing Policies That Would Increase It
Robert F. Kennedy Jr. won applause at the Libertarian National Convention by criticizing government lockdowns and deficit spending, and saying America shouldn't police the world. It made me want to interview him. This month, I did. He said intelligent things about America's growing debt: "President Trump said that he was going to balance the budget and instead he (increased the debt more) than every president in United States history—$8 trillion.
RFK Jr. Pays Lip Service to the Debt While Pushing Policies That Would Increase It

Robert F. Kennedy Jr. won applause at the Libertarian National Convention by criticizing government lockdowns and deficit spending, and saying America shouldn't police the world.
It made me want to interview him. This month, I did.
He said intelligent things about America's growing debt:
"President Trump said that he was going to balance the budget and instead he (increased the debt more) than every president in United States history—$8 trillion. President Biden is on track now to beat him."
It's good to hear a candidate actually talk about our debt.
"When the debt is this large…you have to cut dramatically, and I'm going to do that," he says.
But looking at his campaign promises, I don't see it.
He promises "affordable" housing via a federal program backing 3 percent mortgages.
"Imagine that you had a rich uncle who was willing to cosign your mortgage!" gushes his campaign ad. "I'm going to make Uncle Sam that rich uncle!"
I point out that such giveaways won't reduce our debt.
"That's not a giveaway," Kennedy replies. "Every dollar that I spend as president is going to go toward building our economy."
That's big government nonsense, like his other claim: "Every million dollars we spend on child care creates 22 jobs!"
Give me a break.
When I pressed him about specific cuts, Kennedy says, "I'll cut the military in half…cut it to about $500 billion….We are not the policemen of the world."
"Stop giving any money to Ukraine?" I ask.
"Negotiate a peace," Kennedy replies. "Biden has never talked to Putin about this, and it's criminal."
He never answered whether he'd give money to Ukraine. He did answer about Israel.
"Yes, of course we should,"
"[Since] you don't want to cut this spending, what would you cut?"
"Israel spending is rather minor," he responds. "I'm going to pick the most wasteful programs, put them all in one bill, and send them to Congress with an up and down vote."
Of course, Congress would just vote it down.
Kennedy's proposed cuts would hardly slow down our path to bankruptcy. Especially since he also wants new spending that activists pretend will reduce climate change.
At a concert years ago, he smeared "crisis" skeptics like me, who believe we can adjust to climate change, screaming at the audience, "Next time you see John Stossel and [others]… these flat-earthers, these corporate toadies—lying to you. This is treason, and we need to start treating them now as traitors!"
Now, sitting with him, I ask, "You want to have me executed for treason?"
"That statement," he replies, "it's not a statement that I would make today….Climate is existential. I think it's human-caused climate change. But I don't insist other people believe that. I'm arguing for free markets and then the lowest cost providers should prevail in the marketplace….We should end all subsidies and let the market dictate."
That sounds good: "Let the market dictate."
But wait, Kennedy makes money from solar farms backed by government guaranteed loans. He "leaned on his contacts in the Obama administration to secure a $1.6 billion loan guarantee," wrote The New York Times.
"Why should you get a government subsidy?" I ask.
"If you're creating a new industry," he replies, "you're competing with the Chinese. You want the United States to own pieces of that industry."
I suppose that means his government would subsidize every industry leftists like.
Yet when a wind farm company proposed building one near his family's home, he opposed it.
"Seems hypocritical," I say.
"We're exterminating the right whale in the North Atlantic through these wind farms!" he replies.
I think he was more honest years ago, when he complained that "turbines…would be seen from Cape Cod, Martha's Vineyard… Nantucket….[They] will steal the stars and nighttime views."
Kennedy was once a Democrat, but now Democrats sue to keep him off ballots. Former Clinton Labor Secretary Robert Reich calls him a "dangerous nutcase."
Kennedy complains that Reich won't debate him.
"Nobody will," he says. "They won't have me on any of their networks."
Well, obviously, I will.
I especially wanted to confront him about vaccines.
In a future column, Stossel TV will post more from our hourlong discussion.
COPYRIGHT 2024 BY JFS PRODUCTIONS INC.
The post RFK Jr. Pays Lip Service to the Debt While Pushing Policies That Would Increase It appeared first on Reason.com.

-
Semiconductor Engineering

-
Chip Industry Week In Review
President Biden will raise the tariff rate on Chinese semiconductors from 25% to 50% by 2025, among other measures to protect U.S. businesses from China’s trade practices. Also, as part of President Biden’s AI Executive Order, the Administration released steps to protect workers from AI risks, including human oversight of systems and transparency about what systems are being used. Intel is in advanced talks with Apollo Global Management for the equity firm to provide more than $11 billion to bui
Chip Industry Week In Review
President Biden will raise the tariff rate on Chinese semiconductors from 25% to 50% by 2025, among other measures to protect U.S. businesses from China’s trade practices. Also, as part of President Biden’s AI Executive Order, the Administration released steps to protect workers from AI risks, including human oversight of systems and transparency about what systems are being used.
Intel is in advanced talks with Apollo Global Management for the equity firm to provide more than $11 billion to build a fab in Ireland, reported the Wall Street Journal. Also, Intel’s Foundry Services appointed Kevin O’Buckley as the senior vice president and general manager.
Polar is slated to receive up to $120 million in CHIPS Act funding to establish an independent American foundry in Minnesota. The company expects to invest about $525 million in the expansion of the facility over the next two years, with a $75 million investment from the State of Minnesota.
Arm plans to develop AI chips for launch next year, reports Nikkei Asia.
South Korea is planning a support package worth more than 10 trillion won ($7.3 billion) aimed at chip materials, equipment makers, and fabless companies throughout the semiconductor supply chain, according to Reuters.
Quick links to more news:
Global
In-Depth
Markets and Money
Security
Supercomputing
Education and Training
Product News
Research
Events and Further Reading
Global
Edwards opened a new facility in Asan City, South Korea. The 15,000m² factory provides a key production site for abatement systems, and integrated vacuum and abatement systems for semiconductor manufacturing.
France’s courtship with mega-tech is paying off. Microsoft is investing more than US $4 billion to expand its cloud computing and AI infrastructure, including bringing up to 25,000 advanced GPUs to the country by the end of 2025. The “Choose France” campaign also snagged US $1.3 billion from Amazon for cloud infrastructure expansion, genAI and more.
Toyota, Nissan, and Honda are teaming up on AI and chips for next-gen cars with support from Japan’s Ministry of Economy, Trade and Industry, (METI), reports Nikkei Asia.
Meanwhile, IBM and Honda are collaborating on long-term R&D of next-gen technologies for software-defined vehicles (SDV), including chiplets, brain-inspired computing, and hardware-software co-optimization.
Siemens and Foxconn plan to collaborate on global manufacturing processes in electronics, information and communications technology, and electric vehicles (EV).
TSMC confirmed a Q424 construction start date for its first European plant in Dresden, Germany.
Amazon Web Services (AWS) plans to invest €7.8 billion (~$8.4B) in the AWS European Sovereign Cloud in Germany through 2040. The system is designed to serve public sector organizations and customers in highly regulated industries.
In-Depth
Semiconductor Engineering published its Low Power-High Performance newsletter this week, featuring these stories:
-
- Will Domain-Specific ICs Become Ubiquitous?
- Running More Efficient AI/ML Code With Neuromorphic Engines
- Power/Performance Costs In Chip Security
And this week’s Test, Measurement & Analytics newsletter featured these stories:
- Using Predictive Maintenance To Boost IC Manufacturing Efficiency
- The Future Of Fault Coverage In Chips
- Doing More At Functional Test
Markets and Money
The U.S. National Institute of Standards and Technology (NIST) awarded more than $1.2 million to 12 businesses in 8 states under the Small Business Innovation Research (SBIR) Program to fund R&D of products relating to cybersecurity, quantum computing, health care, semiconductor manufacturing, and other critical areas.
Engineering services and consulting company Infosys completed the acquisition of InSemi Technology, a provider of semiconductor design and embedded software development services.
The quantum market, which includes quantum networking and sensors alongside computing, is predicted to grow from $838 million in 2024 to $1.8 billion in 2029, reports Yole.
Shipments of OLED monitors reached about 200,000 units in Q1 2024, a year over year growth of 121%, reports TrendForce.
Global EV sales grew 18% in Q1 2024 with plug-in hybrid electric vehicles (PHEV) sales seeing 46% YoY growth and battery electric vehicle (BEV) sales growing just 7%, according to Counterpoint. China leads global EV sales with 28% YoY growth, while the US grew just 2%. Tesla saw a 9% YoY drop, but topped BEV sales with a 19% market share. BYD grew 13% YoY and exported about 100,000 EVs with 152% YoY growth, mainly in Southeast Asia.
DeepX raised $80.5 million in Series C funding for its on-device NPU IP and AI SoCs tailored for applications including physical security, robotics, and mobility.
MetisX raised $44 million in Series A funding for its memory solutions built on Compute Express Link (CXL) for accelerating large-scale data processing applications.
Security
While security experts have been warning of a growing threat in electronics for decades, there have been several recent fundamental changes that elevate the risk.
Synopsys and the Ponemon Institute released a report showing 54% of surveyed organizations suffered a software supply chain attack in the past year and 20% were not effective in their response. And 52% said their development teams use AI tools to generate code, but only 32% have processes to evaluate it for license, security, and quality risks.
Researchers at Ruhr University Bochum and TU Darmstadt presented a solution for the automated generation of fault-resistant circuits (AGEFA) and assessed the security of examples generated by AGEFA against side-channel analysis and fault injection.
TXOne reported on operational technology security and the most effective method for preventing production interruptions caused by cyber-attacks.
CrowdStrike and NVIDIA are collaborating to accelerate the use of analytics and AI in cybersecurity to help security teams combat modern cyberattacks, including AI-powered threats.
The National Institute of Standards and Technology (NIST) finalized its guidelines for protecting sensitive data, known as controlled unclassified information, aimed at organizations that do business with the federal government.
The Defense Advanced Research Projects Agency (DARPA) awarded BAE Systems a $12 million contract to solve thermal challenges limiting electronic warfare systems, particularly in GaN transistors.
Sigma Defense won a $4.7 million contract from the U.S. Army for an AI-powered virtual training environment, partnering with Brightline Interactive on a system that uses spatial computing and augmented intelligence workflows.
SkyWater’s advanced packaging operation in Florida has been accredited as a Category 1A Trusted Supplier by the Defense Microelectronics Activity (DMEA) of the U.S. Department of Defense (DoD).
Videos of two CWE-focused sessions from CVE/FIRST VulnCon 2024 were made available on the CWE YouTube Channel.
The Cybersecurity and Infrastructure Security Agency (CISA) issued a number of alerts/advisories.
Supercomputing
Supercomputers are battling for top dog.
The Frontier supercomputer at Oak Ridge National Laboratory (ORNL) retained the top spot on the Top500 list of the world’s fastest systems with an HPL score of 1.206 EFlop/s. The as-yet incomplete Aurora system at Argonne took second place, becoming the world’s second exascale system at 1.012 EFlop/s. The Green500 list, which tracks energy efficiency of compute, saw three new entrants take the top places.
Cerebras Systems, Sandia National Laboratory, Lawrence Livermore National Laboratory, and Los Alamos National Laboratory used Cerebras’ second generation Wafer Scale Engine to perform atomic scale molecular dynamics simulations at the millisecond scale, which they claim is 179X faster than the Frontier supercomputer.
UT Austin‘s Stampede3 Supercomputer is now in full production, serving the open science community through 2029.
Education and Training
SEMI announced the SEMI University Semiconductor Certification Programs to help alleviate the workforce skills gap. Its first two online courses are designed for new talent seeking careers in the industry, and experienced workers looking to keep their skills current. Also, SEMI and other partners launched a European Chip Skills Academy Summer School in Italy.
Siemens created an industry credential program for engineering students that supplements a formal degree by validating industry knowledge and skills. Nonprofit agency ABET will provide accreditation. The first two courses are live at the University of Colorado Boulder (CU Boulder) and a series is planned with Pennsylvania State University (Penn State).
Syracuse University launched a $20 million Center for Advanced Semiconductor Manufacturing, with co-funding from Onondaga County.
Starting young is a good thing. An Arizona school district, along with the University Of Arizona, is creating a semiconductor program for high schoolers.
Product News
Siemens and Sony partnered to enable immersive engineering via a spatial content creation system, NX Immersive Designer, which includes Sony’s XR head-mounted display. The integration of hardware and software gives designers and engineers natural ways to interact with a digital twin. Siemens also extended its Xcelerator as a Service portfolio with solutions for product engineering and lifecycle management, cloud-based high-performance simulation, and manufacturing operations management. It will be available on Microsoft Azure, as well.
Advantest announced the newest addition to its portfolio of power supplies for the V93000 EXA Scale SoC test platform. The DC Scale XHC32 power supply offers 32 channels with single-instrument total current of up to 640A.
![]()
Fig. 1: Advantest’s DC Scale XHC32. Source: Advantest
Infineon released its XENSIV TLE49SR angle sensors, which can withstand stray magnetic fields of up to 8 mT, ideal for applications of safety-critical automotive chassis systems.
Google debuted its sixth generation Cloud TPU, 4.7X faster and 67% more energy-efficient than the previous generation, with double the high-bandwidth memory.
X-Silicon uncorked a RISC-V vector CPU, coupled with a Vulkan-enabled GPU ISA and AI/ML acceleration in a single processor core, aimed at embedded and IoT applications.
IBM expanded its Qiskit quantum software stack, including the stable release of its SDK for building, optimizing, and visualizing quantum circuits.
Northeastern University announced the general availability of testing and integration solutions for Open RAN through the Open6G Open Testing and Integration Center (Open 6G OTIC).
Research
The University of Glasgow received £3 million (~$3.8M) from the Engineering and Physical Sciences Research Council (EPSRC)’s Strategic Equipment Grant scheme to help establish “Analogue,” an Automated Nano Analysing, Characterisation and Additive Packaging Suite to research silicon chip integration and packaging.
EPFL researchers developed scalable photonic ICs, based on lithium tantalate.
DISCO developed a way to increase the diameter of diamond wafers that uses the KABRA process, a laser ingot slicing method.
CEA-Leti developed two complementary approaches for high performance photon detectors — a mercury cadmium telluride-based avalanche photodetector and a superconducting single photon detector.
Toshiba demonstrated storage capacities of over 30TB with two next-gen large capacity recording technologies for hard disk drives (HDDs): Heat Assisted Magnetic Recording (HAMR) and Microwave Assisted Magnetic Recording (MAMR).
Caltech neuroscientists reported that their brain-machine interface (BMI) worked successfully in a second human patient, following 2022’s first instance, proving the device is not dependent on one particular brain or one location in a brain.
Linköping University researchers developed a cheap, sustainable battery made from zinc and lignin, while ORNL researchers developed carbon-capture batteries.
Events and Further Reading
Find upcoming chip industry events here, including:
| Event | Date | Location |
|---|---|---|
| European Test Symposium | May 20 – 24 | The Hague, Netherlands |
| NI Connect Austin 2024 | May 20 – 22 | Austin, Texas |
| ITF World 2024 (imec) | May 21 – 22 | Antwerp, Belgium |
| Embedded Vision Summit | May 21 – 23 | Santa Clara, CA |
| ASIP Virtual Seminar 2024 | May 22 | Online |
| Electronic Components and Technology Conference (ECTC) 2024 | May 28 – 31 | Denver, Colorado |
| Hardwear.io Security Trainings and Conference USA 2024 | May 28 – Jun 1 | Santa Clara, CA |
| SW Test | Jun 3 – 5 | Carlsbad, CA |
| IITC2024: Interconnect Technology Conference | Jun 3 – 6 | San Jose, CA |
| VOICE Developer Conference | Jun 3 – 5 | La Jolla, CA |
| CHIPS R&D Standardization Readiness Level Workshop | Jun 4 – 5 | Online and Boulder, CO |
| Find All Upcoming Events Here | ||
Upcoming webinars are here.
Semiconductor Engineering’s latest newsletters:
Automotive, Security and Pervasive Computing
Systems and Design
Low Power-High Performance
Test, Measurement and Analytics
Manufacturing, Packaging and Materials
The post Chip Industry Week In Review appeared first on Semiconductor Engineering.
-
Latest
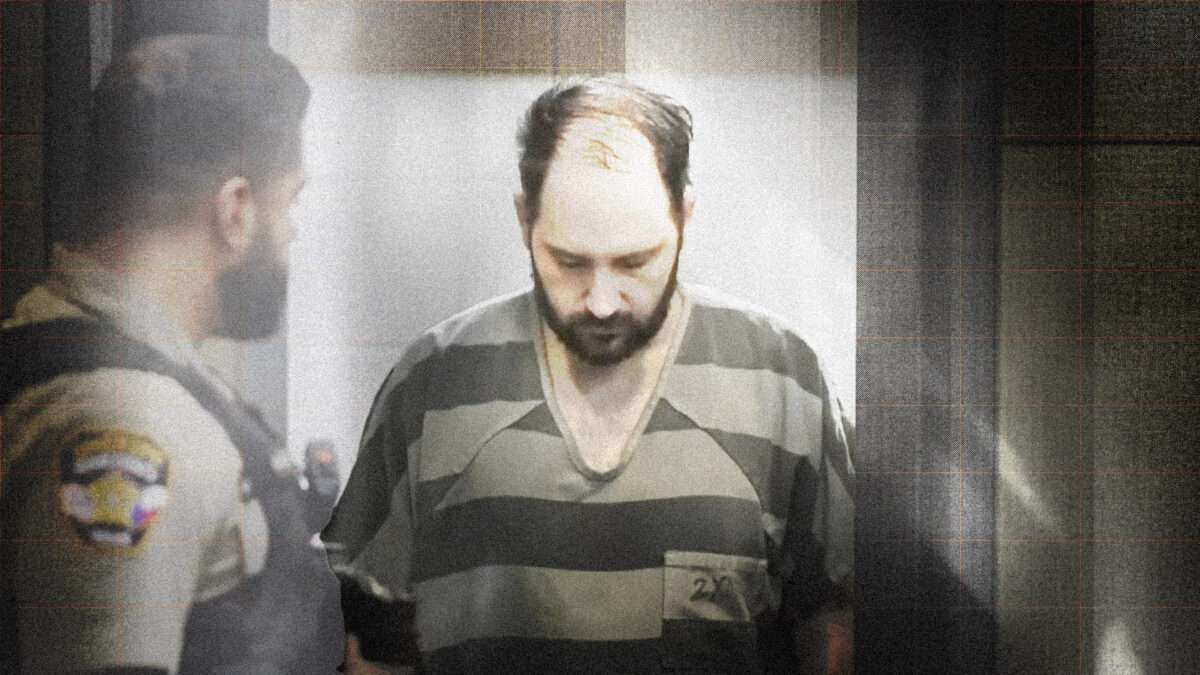
-
Daniel Perry's Pardon Makes a Mockery of Self-Defense
That there are government officials who politicize the law is about as foundational to the discourse as any complaint I can think of. The criticism is sometimes quite fair. And for the latest example of a soft-on-crime politician flouting law and order, we can look to Texas Gov. Greg Abbott. Abbott, of course, is no self-styled progressive. But his recent decision to pardon Daniel Perry, who was convicted last year of murdering Garrett Foster, ch
Daniel Perry's Pardon Makes a Mockery of Self-Defense

That there are government officials who politicize the law is about as foundational to the discourse as any complaint I can think of. The criticism is sometimes quite fair. And for the latest example of a soft-on-crime politician flouting law and order, we can look to Texas Gov. Greg Abbott.
Abbott, of course, is no self-styled progressive. But his recent decision to pardon Daniel Perry, who was convicted last year of murdering Garrett Foster, channels the spirit of the progressive prosecutors he criticizes for allegedly refashioning the law to suit their ideological preferences. He just has different targets.
The governor, who last year urged the Texas Board of Pardons and Paroles to recommend a pardon for Perry, doesn't see it that way. "Texas has one of the strongest 'Stand Your Ground' laws of self-defense that cannot be nullified by a jury or a progressive District Attorney," he wrote in a statement yesterday, approving the pardon after the board officially obliged his request. (It's worth noting that the board, whose members are appointed by the governor, circumvented its own requirement that "evidence of actual innocence from at least two trial officials, or the findings of fact and conclusions of law from the district judge indicating actual innocence" be submitted to even consider such a pardon.)
It is absolutely true that the right to self-defense is vital. And to argue that Perry—who, prior to killing Foster at a 2020 Black Lives Matter protest, wrote that he wanted to "shoot the [protesters] in the front and push the pedal to the metal"—acted in self-defense is to make a total mockery of that right and those who've had to exercise it.
It is also true that many district attorneys, some of them so-called "progressive" prosecutors, appear to disdain that right. There are the cases across New York City I've covered, for example, where prosecutors are unconscionably seeking lengthy prison terms for people who acted in self-defense but had the audacity to do so with an unlicensed gun. That includes the case of Charles Foehner, an elderly man who shot a mugger in Queens, after which law enforcement brought so many weapons charges against him that Foehner would go to prison for life if convicted on all. That was in June 2023. In November, LaShawn Craig of Brooklyn shot a masked man who'd entered his apartment. Though prosecutors concede the shooting was in self-defense, they also charged him with several weapons offenses, including criminal possession of a weapon, a violent felony.
And then, most famously, there was Kyle Rittenhouse, whose 2021 prosecution for murder polarized much of the nation, despite that, if you knew the facts, it was an obvious example of self-defense—something I made very clear at the time.
There are some interesting parallels between Rittenhouse's case and Perry's case that are hard to ignore. Both men used their guns at protests against police brutality, many of which popped up across the U.S. in the summer of 2020. The shootings happened exactly a month apart. Then their stories diverge considerably, ending in an acquittal and a conviction, because the way they used their firearms was quite different, despite the culture war backdrop being the same. Both of these things can be true.
In July 2020, Perry ran a red light and drove into a crowd of protesters. That in and of itself, of course, is not enough to deduce that he was looking for a fight. His own statements prior to doing so, however, add a great deal of helpful context and show his frame of mind at the time. "I might have to kill a few people on my way to work they are rioting outside my apartment complex," he wrote on social media on May 31, 2020. Also in May, he threatened to a friend that he "might go to Dallas to shoot looters." And then in mid-June, he sent that message about going to a protest, "shoot[ing] the ones in the front," and then careening his car through the hubbub.
This was part of a pattern. Austin police detective William Bursley testified, for instance, that Perry searched on Safari for "protesters in Seattle gets shot," "riot shootouts," and "protests in Dallas live." It is not hard to connect the dots between his searches and messages.
So what about that stand-your-ground defense Abbott alleges the jury nullified? Core to Perry's case and trial was whether he reasonably feared for his life that July evening. Foster indeed had a rifle on him—because open carry is legal in Texas. The Second Amendment does not solely exist for people with conservative views. The big question then: Was Foster pointing the gun at Perry when he approached his vehicle? For the answer, we can go to Perry himself, who told law enforcement that he was not. "I believe he was going to aim at me," he said. "I didn't want to give him a chance to aim at me." But that is not a self-defense justification, as Perry cannot claim clairvoyance.
That the jury reached the conclusion they did is not a mystery, nor is it an outrage. What is outrageous, however, is that a governor who claims to care about law and order has made clear that his support for crime victims is at least in part conditional on having the "right" politics.
The post Daniel Perry's Pardon Makes a Mockery of Self-Defense appeared first on Reason.com.

-
Latest

-
World War War III May Already Have Started—in the Shadows
Britain's signals intelligence spy chief raised eyebrows this week with warnings that Russia is coordinating both cyberattacks and physical acts of sabotage against the West. There's evidence to back her claims—and the West may be returning the favor. Coming soon after FBI Director Christopher Wray warned that China is targeting American infrastructure, it looks like the world is not only fracturing once again, but that the hostile blocs are enga
World War War III May Already Have Started—in the Shadows

Britain's signals intelligence spy chief raised eyebrows this week with warnings that Russia is coordinating both cyberattacks and physical acts of sabotage against the West. There's evidence to back her claims—and the West may be returning the favor. Coming soon after FBI Director Christopher Wray warned that China is targeting American infrastructure, it looks like the world is not only fracturing once again, but that the hostile blocs are engaged in covert warfare.
Rumors of War
"We are increasingly concerned about growing links between the Russian intelligence services and proxy groups to conduct cyberattacks as well as suspected physical surveillance and sabotage operations," Government Communications Headquarters (GCHQ) Director Anne Keast-Butler told an audience at the United Kingdom government-sponsored CyberUK 2024 conference. "Before, Russia simply created the right environments for these groups to operate, but now they are nurturing and inspiring these non-state cyber actors in some cases seemingly coordinating physical attacks against the West."
Keast-Butler, whose agency is comparable to the U.S. National Security Agency (NSA), also called out China, Iran, and North Korea as cybersecurity dangers. But naming Russian officials as being behind "physical attacks" raises the stakes. Sadly, her claims are well-founded.
Sabotage, Espionage, and Other Mischief
"A 20-year-old British man has been charged with masterminding an arson plot against a Ukrainian-linked target in London for the benefit of the Russian state," CBS News reported last month. That wasn't an isolated incident.
"In April alone a clutch of alleged pro-Russian saboteurs were detained across the continent," The Economist noted May 12 in describing what it called a "shadow war" between East and West. "Germany arrested two German-Russian dual nationals on suspicion of plotting attacks on American military facilities and other targets on behalf of the GRU, Russia's military intelligence agency. Poland arrested a man who was preparing to pass the GRU information on Rzeszow airport, the most important hub for military aid to Ukraine. Britain charged several men over an earlier arson attack in March on a Ukrainian-owned logistics firm in London whose Spanish depot was also targeted."
The GCHQ chief's warnings coupled with reality on the ground are alarming in themselves. Worse, they come after FBI Director Christopher Wray issued similar cautions in April about China.
"The PRC [People's Republic of China] has made it clear that it considers every sector that makes our society run as fair game in its bid to dominate on the world stage, and that its plan is to land low blows against civilian infrastructure to try to induce panic and break America's will to resist," Wray told the Vanderbilt Summit on Modern Conflict and Emerging Threats in Nashville, Tennessee.
Wray clarified that, by "infrastructure," he meant "everything from water treatment facilities and energy grids to transportation and information technology."
If that doesn't make you want to check that your pantry is stocked and that the water filter and generator are in working order, nothing will.
A Game Both Sides Can Play
Of course, in war of any sort, the implication is that both sides are involved in conflict. Western intelligence officials are loud in their warnings about foreign threats, but less open regarding just what their own operatives might be doing in Russia, China, and elsewhere. Still, there's evidence that this is hardly a one-sided war, shadowy though it may be.
In June 2022, The New York Times reported that Ukraine's defensive efforts relied heavily on "a stealthy network of commandos and spies rushing to provide weapons, intelligence and training." In addition to Americans, the story noted, "commandos from other NATO countries, including Britain, France, Canada and Lithuania, also have been working inside Ukraine."
American journalist and combat veteran Jack Murphy goes further, claiming the CIA, working through an allied spy service "is responsible for many of the unexplained explosions and other mishaps that have befallen the Russian military industrial complex." The targets include "railway bridges, fuel depots and power plants," he adds.
And if you wonder who blew up Nord Stream 1 and 2, well, so do a lot of people. Russia was initially accused, but it didn't make a lot of sense for the country's forces to destroy pipelines that generated revenue and fed western dependence on Russian natural gas. Since then, Denmark and Sweden have closed inconclusive investigations, journalist Seymour Hersh blamed American officials, and a report by Der Spiegel and The Washington Post placed responsibility on a rogue Ukrainian military officer.
The Wider War Is Here
Taken all together, the warnings from Keast-Butler and Wray, as well as acts of sabotage and arrests of foreign agents suggest that fears of a wider war resulting from Russia's continuing invasion of Ukraine may miss the point; the war could already be here. People looking for tanks and troops are overlooking cyber intrusions, arson, bombings, and other low-level mayhem.
"Russia is definitely at war with the West," Oleksandr Danylyuk of the Royal United Services Institute, a British defense and security think tank, told NBC News earlier this week.
Russian officials seem to embrace that understanding, with Kremlin spokesman Dmitry Peskov commenting in March that the invasion of Ukraine, originally referred to by the euphemism "special military operation," is now more serious. "It has become a war for us as the collective West more and more directly increases its level of involvement in the conflict," he said.
Fortunately, a shadow war of the sort around us is less destructive than open military conflict, especially when the hostilities involve nuclear-armed powers. It's far better that spies hack the email accounts of government officials, as happened in the case of a Russian cyberattack on Germany's ruling Social Democrats, than that cities burn. But civilians still must live with the consequences of combatants attempting to do each other harm—particularly when the harm is to infrastructure on which regular people rely.
So, welcome to the world of global shadow war. Try to not become collateral damage.
The post World War War III May Already Have Started—in the Shadows appeared first on Reason.com.

-
Ars Technica - All content

-
Leaks from Valve’s Deadlock look like a pressed sandwich of every game around
Enlarge / Valve has its own canon of games full of artifacts and concepts worth emulating, as seen in a 2018 tour of its offices. (credit: Sam Machkovech) "Basically, fast-paced interesting ADHD gameplay. Combination of Dota 2, Team Fortress 2, Overwatch, Valorant, Smite, Orcs Must Die." That's how notable Valve leaker "Gabe Follower" describes Deadlock, a Valve game that is seemingly in playtesting at the moment, for which a few screenshots have leaked out. The game has been
Leaks from Valve’s Deadlock look like a pressed sandwich of every game around

Enlarge / Valve has its own canon of games full of artifacts and concepts worth emulating, as seen in a 2018 tour of its offices. (credit: Sam Machkovech)
"Basically, fast-paced interesting ADHD gameplay. Combination of Dota 2, Team Fortress 2, Overwatch, Valorant, Smite, Orcs Must Die."
That's how notable Valve leaker "Gabe Follower" describes Deadlock, a Valve game that is seemingly in playtesting at the moment, for which a few screenshots have leaked out.
The game has been known as "Neon Prime" and "Citadel" at prior points. It's a "Competitive third-person hero-based shooter," with six-on-six battles across a map with four "lanes." That allows for some of the "Tower defense mechanics" mentioned by Gabe Follower, along with "fast travel using floating rails, similar to Bioshock Infinite." The maps reference a "modern steampunk European city (little bit like Half-Life)," after "bad feedback" about a sci-fi theme pushed the development team toward fantasy.
-
Semiconductor Engineering

-
Using AI/ML To Combat Cyberattacks
Machine learning is being used by hackers to find weaknesses in chips and systems, but it also is starting to be used to prevent breaches by pinpointing hardware and software design flaws. To make this work, machine learning (ML) must be trained to identify vulnerabilities, both in hardware and software. With proper training, ML can detect cyber threats and prevent them from accessing critical data. As ML encounters additional cyberattack scenarios, it can learn and adapt, helping to build a mor
Using AI/ML To Combat Cyberattacks
Machine learning is being used by hackers to find weaknesses in chips and systems, but it also is starting to be used to prevent breaches by pinpointing hardware and software design flaws.
To make this work, machine learning (ML) must be trained to identify vulnerabilities, both in hardware and software. With proper training, ML can detect cyber threats and prevent them from accessing critical data. As ML encounters additional cyberattack scenarios, it can learn and adapt, helping to build a more sophisticated defense system that includes hardware, software, and how they interface with larger systems. It also can automate many cyber defense tasks with minimum human intervention, which saves time, effort, and money.
ML is capable of sifting through large volumes of data much faster than humans. Potentially, it can reduce or remove human errors, lower costs, and boost cyber defense capability and overall efficiency. It also can perform such tasks as connection authentication, system design, vulnerability detection, and most important, threat detection through pattern and behavioral analysis.
“AI/ML is finding many roles protecting and enhancing security for digital devices and services,” said David Maidment, senior director of market development at Arm. “However, it is also being used as a tool for increasingly sophisticated attacks by threat actors. AI/ML is essentially a tool tuned for very advanced pattern recognition across vast data sets. Examples of how AI/ML can enhance security include network-based monitoring to spot rogue behaviors at scale, code analysis to look for vulnerabilities on new and legacy software, and automating the deployment of software to keep devices up-to-date and secure.”
This means that while AI/ML can be used as a force for good, inevitably bad actors will use it to increase the sophistication and scale of attacks. “Building devices and services based on security best practices, having a hardware-protected root of trust (RoT), and an industry-wide methodology to standardize and measure security are all essential,” Maidment said. “The focus on security, including the rapid growth of AI/ML, is certainly driving industry and government discussions as we work on solutions to maximize AI/ML’s benefits and minimize any potential harmful impact.”
Zero trust is a fundamental requirement when it comes to cybersecurity. Before a user or device is allowed to connect to the network or server, requests have to be authenticated to make sure they are legitimate and authorized. ML will enhance the authentication process, including password management, phishing prevention, and malware detection.
Areas that bad actors look to exploit are software design vulnerabilities and weak points in systems and networks. Once hackers uncover these vulnerabilities, they can be used as a point of entrance to the network or systems. ML can detect these vulnerabilities and alert administrators.
Taking a proactive approach by doing threat detection is essential in cyber defense. ML pattern and behavioral analysis strengths support this strategy. When ML detects unusual behavior in data traffic flow or patterns, it sends an alert about abnormal behavior to the administrator. This is similar to the banking industry’s practice of watching for credit card use that does not follow an established pattern. A large purchase overseas on a credit card with a pattern of U.S. use only for moderate amounts would trigger an alert, for example.
As hackers become more sophisticated with new attack vectors, whether it is new ransomware or distributed denial of service (DDoS) attacks, ML will do a much better job than humans in detecting these unknown threats.
Limitations of ML in cybersecurity
While ML provides many benefits, its value depends on the data used to train it. The more that can be used to train the ML model, the better it is at detecting fraud and cyber threats. But acquiring this data raises overall cybersecurity system design expenses. The model also needs constant maintenance and tuning to sustain peak performance and meet the specific needs of users. And while ML can do many of the tasks, it still requires some human involvement, so it’s essential to understand both cybersecurity and how well ML functions.
While ML is effective in fending off many of the cyberattacks, it is not a panacea. “The specific type of artificial intelligence typically referenced in this context is machine learning (ML), which is the development of algorithms that can ingest large volumes of training data, then generalize and make meaningful observations and decisions based on novel data,” said Scott Register, vice president of security solutions at Keysight Technologies. “With the right algorithms and training, AI/ML can be used to pinpoint cyberattacks which might otherwise be difficult to detect.”
However, no one — at least in the commercial space — has delivered a product that can detect very subtle cyberattacks with complete accuracy. “The algorithms are getting better all the time, so it’s highly probable that we’ll soon have commercial products that can detect and respond to attacks,” Register said. “We must keep in mind, however, that attackers don’t sit still, and they’re well-funded and patient. They employ ‘offensive AI,’ which means they use the same types of techniques and algorithms to generate attacks which are unlikely to be detected.”
ML implementation considerations
For any ML implementation, a strong cyber defense system is essential, but there’s no such thing as a completely secure design. Instead, security is a dynamic and ongoing process that requires constant fine-tuning and improvement against ever-changing cyberattacks. Implementing ML requires a clear security roadmap, which should define requirements. It also requires implementing a good cybersecurity process, which secures individual hardware and software components, as well as some type of system testing.
“One of the things we advise is to start with threat modeling to identify a set of critical design assets to protect from an adversary under confidentiality or integrity,” said Jason Oberg, CTO at Cycuity. “From there, you can define a set of very succinct, secure requirements for the assets. All of this work is typically done at the architecture level. We do provide education, training and guidance to our customers, because at that level, if you don’t have succinct security requirements defined, then it’s really hard to verify or check something in the design. What often happens is customers will say, ‘I want to have a secure chip.’ But it’s not as easy as just pressing a button and getting a green check mark that confirms the chip is now secure.”
To be successful, engineering teams must start at the architectural stages and define the security requirements. “Once that is done, they can start actually writing the RTL,” Oberg said. “There are tools available to provide assurances these security requirements are being met, and run within the existing simulation and emulation environments to help validate the security requirements, and help identify any unknown design weaknesses. Generally, this helps hardware and verification engineers increase their productivity and build confidence that the system is indeed meeting the security requirements.”
![]()
Fig. 1: A cybersecurity model includes multiple stages, progressing from the very basic to in-depth. It is important for organizations to know what stages their cyber defense system are. Source: Cycuity
Steve Garrison, senior vice president, marketing of Stellar Cyber, noted that if cyber threats were uncovered during the detection process, so many data files may be generated that they will be difficult for humans to sort through. Graphical displays can speed up the process and reduce the overall mean time to detection (MTTD) and mean time to response (MTTR).
![]()
Fig. 2: Using graphical displays would reduce the overall meantime to detection (MTTD) and meantime to response (MTTR). Source: Stellar Cyber
Testing is essential
Another important stage in the design process is testing, whereby each system design requires a vigorous attack simulation tool to weed out the basic oversights to ensure it meets the predefined standard.
“First, if you want to understand how defensive systems will function in the real world, it’s important to test them under conditions, which are as realistic as possible,” Keysight’s Register said. “The network environment should have the same amount of traffic, mix of applications, speeds, behavioral characteristics, and timing as the real world. For example, the timing of a sudden uptick in email and social media traffic corresponds to the time when people open up their laptops at work. The attack traffic needs to be as realistic as possible as well – hackers try hard not to be noticed, often preferring ‘low and slow’ attacks, which may take hours or days to complete, making detection much more difficult. The same obfuscation techniques, encryption, and decoy traffic employed by threat actors needs to be simulated as accurately as possible.”
Further, due to mistaken assumptions during testing, defensive systems often perform great in the lab, yet fail spectacularly in production networks. “Afterwards we hear, for example, ‘I didn’t think hackers would encrypt their malware,’ or ‘Internal e-mails weren’t checked for malicious attachments, only those from external senders,’” Register explained. “Also, in security testing, currency is key. Attacks and obfuscation techniques are constantly evolving. If a security system is tested against stale attacks, then the value of that testing is limited. The offensive tools should be kept as up to date as possible to ensure the most effective performance against the tools a system is likely to encounter in the wild.”
Semiconductor security
Almost all system designs depend on semiconductors, so it is important to ensure that any and all chips, firmware, FPGAs, and SoCs are secure – including those that perform ML functionality.
“Semiconductor security is a constantly evolving problem and requires an adaptable solution, said Jayson Bethurem, vice president marketing and business development at Flex Logix. “Fixed solutions with current cryptography that are implemented today will inevitably be challenged in the future. Hackers today have more time, resources, training, and motivation to disrupt technology. With technology increasing in every facet of our lives, defending against this presents a real challenge. We also have to consider upcoming threats, namely quantum computing.”
Many predict that quantum computing will be able to crack current cryptography solutions in the next few years. “Fortunately, semiconductor manufacturers have solutions that can enable cryptography agility, which can dynamically adapt to evolving threats,” Bethurem said. “This includes both updating hardware accelerated cryptography algorithms and obfuscating them, an approach that increases root of trust and protects valuable IP secrets. Advanced solutions like these also involve devices randomly creating their own encryption keys, making it harder for algorithms to crack encryption codes.”
Advances in AI/ML algorithms can adapt to new threats and reduce latency of algorithm updates from manufacturers. This is particularly useful with reconfigurable eFPGA IP, which can be implemented into any semiconductor device to thwart all current and future threats and optimized to run AI/ML-based cryptography solutions. The result is a combination of high-performance processing, scalability, and low-latency attack response.
Chips that support AI/ML algorithms need not only computing power, but also accelerators for those algorithms. In addition, all of this needs to happen without exceeding a tight power budget.
“More AI/ML systems run at tiny edges rather than at the core,” said Detlef Houdeau, senior director of design system architecture at Infineon Technologies. “AI/ML systems don’t need any bigger computer and/or cloud. For instance, a Raspberry Pi for a robot in production can have more than 3 AI/ML algorithms working in parallel. A smartphone has more than 10 AI/ML functions in the phone, and downloading new apps brings new AI/ML algorithms into the device. A pacemaker can have 2 AI/ML algorithms. Security chips, meanwhile, need a security architecture as well as accelerators for encryption. Combining an AI/ML accelerator with an encryption accelerator in the same chip could increase the performance in microcontroller units, and at the same time foster more security at the edge. The next generation of microelectronics could show this combination.”
After developers have gone through design reviews and the systems have run vigorous tests, it helps to have third-party certification and/or credentials to ensure the systems are indeed secure from a third-party independent viewpoint.
“As AI, and recently generative AI, continue to transform all markets, there will be new attack vectors to mitigate against,” said Arm’s Maidment. “We expect to see networks become smarter in the way they monitor traffic and behaviors. The use of AI/ML allows network-based monitoring at scale to allow potential unexpected or rogue behavior to be identified and isolated. Automating network monitoring based on AI/ML will allow an extra layer of defense as networks scale out and establish effectively a ‘zero trust’ approach. With this approach, analysis at scale can be tuned to look at particular threat vectors depending on the use case.”
With an increase in AI/ML adoption at the edge, a lot of this is taking place on the CPU. “Whether it is handling workloads in their entirety, or in combination with a co-processor like a GPU or NPU, how applications are deployed across the compute resources needs to be secure and managed centrally within the edge AI/ML device,” Maidment said. “Building edge AI/ML devices based on a hardware root of trust is essential. It is critical to have privileged access control of what code is allowed to run where using a trusted memory management architecture. Arm continually invests in security, and the Armv9 architecture offers a number of new security features. Alongside architecture improvements, we continue to work in partnership with the industry on our ecosystem security framework and certification scheme, PSA Certified, which is based on a certified hardware RoT. This hardware base helps to improve the security of systems and fulfill the consumer expectation that as devices scale, they remain secure.”
Outlook
It is important to understand that threat actors will continue to evolve attacks using AI/ML. Experts suggest that to counter such attacks, organizations, institutions, and government agencies will have to continually improve defense strategies and capabilities, including AI/ML deployment.
AI/ML can be used as weapon from an attacker for industrial espionage and/or industrial sabotage, and stopping incursions will require a broad range of cyberattack prevention and detection tools, including AI/ML functionality for anomaly detection. But in general, hackers are almost always one step ahead.
According to Register, “the recurring cycle is: 1) hackers come out with a new tool or technology that lets them attack systems or evade detection more effectively; 2) those attacks cause enough economic damage that the industry responds and develops effective countermeasures; 3) the no-longer-new hacker tools are still employed effectively, but against targets that haven’t bothered to update their defenses; 4) hackers develop new offensive tools that are effective against the defensive techniques of high-value targets, and the cycle starts anew.”
Related Reading
Securing Chip Manufacturing Against Growing Cyber Threats
Suppliers are the number one risk, but reducing attacks requires industry-wide collaboration.
Data Center Security Issues Widen
The number and breadth of hardware targets is increasing, but older attack vectors are not going away. Hackers are becoming more sophisticated, and they have a big advantage.
The post Using AI/ML To Combat Cyberattacks appeared first on Semiconductor Engineering.
-
Semiconductor Engineering

-
Using AI/ML To Combat Cyberattacks
Machine learning is being used by hackers to find weaknesses in chips and systems, but it also is starting to be used to prevent breaches by pinpointing hardware and software design flaws. To make this work, machine learning (ML) must be trained to identify vulnerabilities, both in hardware and software. With proper training, ML can detect cyber threats and prevent them from accessing critical data. As ML encounters additional cyberattack scenarios, it can learn and adapt, helping to build a mor
Using AI/ML To Combat Cyberattacks
Machine learning is being used by hackers to find weaknesses in chips and systems, but it also is starting to be used to prevent breaches by pinpointing hardware and software design flaws.
To make this work, machine learning (ML) must be trained to identify vulnerabilities, both in hardware and software. With proper training, ML can detect cyber threats and prevent them from accessing critical data. As ML encounters additional cyberattack scenarios, it can learn and adapt, helping to build a more sophisticated defense system that includes hardware, software, and how they interface with larger systems. It also can automate many cyber defense tasks with minimum human intervention, which saves time, effort, and money.
ML is capable of sifting through large volumes of data much faster than humans. Potentially, it can reduce or remove human errors, lower costs, and boost cyber defense capability and overall efficiency. It also can perform such tasks as connection authentication, system design, vulnerability detection, and most important, threat detection through pattern and behavioral analysis.
“AI/ML is finding many roles protecting and enhancing security for digital devices and services,” said David Maidment, senior director of market development at Arm. “However, it is also being used as a tool for increasingly sophisticated attacks by threat actors. AI/ML is essentially a tool tuned for very advanced pattern recognition across vast data sets. Examples of how AI/ML can enhance security include network-based monitoring to spot rogue behaviors at scale, code analysis to look for vulnerabilities on new and legacy software, and automating the deployment of software to keep devices up-to-date and secure.”
This means that while AI/ML can be used as a force for good, inevitably bad actors will use it to increase the sophistication and scale of attacks. “Building devices and services based on security best practices, having a hardware-protected root of trust (RoT), and an industry-wide methodology to standardize and measure security are all essential,” Maidment said. “The focus on security, including the rapid growth of AI/ML, is certainly driving industry and government discussions as we work on solutions to maximize AI/ML’s benefits and minimize any potential harmful impact.”
Zero trust is a fundamental requirement when it comes to cybersecurity. Before a user or device is allowed to connect to the network or server, requests have to be authenticated to make sure they are legitimate and authorized. ML will enhance the authentication process, including password management, phishing prevention, and malware detection.
Areas that bad actors look to exploit are software design vulnerabilities and weak points in systems and networks. Once hackers uncover these vulnerabilities, they can be used as a point of entrance to the network or systems. ML can detect these vulnerabilities and alert administrators.
Taking a proactive approach by doing threat detection is essential in cyber defense. ML pattern and behavioral analysis strengths support this strategy. When ML detects unusual behavior in data traffic flow or patterns, it sends an alert about abnormal behavior to the administrator. This is similar to the banking industry’s practice of watching for credit card use that does not follow an established pattern. A large purchase overseas on a credit card with a pattern of U.S. use only for moderate amounts would trigger an alert, for example.
As hackers become more sophisticated with new attack vectors, whether it is new ransomware or distributed denial of service (DDoS) attacks, ML will do a much better job than humans in detecting these unknown threats.
Limitations of ML in cybersecurity
While ML provides many benefits, its value depends on the data used to train it. The more that can be used to train the ML model, the better it is at detecting fraud and cyber threats. But acquiring this data raises overall cybersecurity system design expenses. The model also needs constant maintenance and tuning to sustain peak performance and meet the specific needs of users. And while ML can do many of the tasks, it still requires some human involvement, so it’s essential to understand both cybersecurity and how well ML functions.
While ML is effective in fending off many of the cyberattacks, it is not a panacea. “The specific type of artificial intelligence typically referenced in this context is machine learning (ML), which is the development of algorithms that can ingest large volumes of training data, then generalize and make meaningful observations and decisions based on novel data,” said Scott Register, vice president of security solutions at Keysight Technologies. “With the right algorithms and training, AI/ML can be used to pinpoint cyberattacks which might otherwise be difficult to detect.”
However, no one — at least in the commercial space — has delivered a product that can detect very subtle cyberattacks with complete accuracy. “The algorithms are getting better all the time, so it’s highly probable that we’ll soon have commercial products that can detect and respond to attacks,” Register said. “We must keep in mind, however, that attackers don’t sit still, and they’re well-funded and patient. They employ ‘offensive AI,’ which means they use the same types of techniques and algorithms to generate attacks which are unlikely to be detected.”
ML implementation considerations
For any ML implementation, a strong cyber defense system is essential, but there’s no such thing as a completely secure design. Instead, security is a dynamic and ongoing process that requires constant fine-tuning and improvement against ever-changing cyberattacks. Implementing ML requires a clear security roadmap, which should define requirements. It also requires implementing a good cybersecurity process, which secures individual hardware and software components, as well as some type of system testing.
“One of the things we advise is to start with threat modeling to identify a set of critical design assets to protect from an adversary under confidentiality or integrity,” said Jason Oberg, CTO at Cycuity. “From there, you can define a set of very succinct, secure requirements for the assets. All of this work is typically done at the architecture level. We do provide education, training and guidance to our customers, because at that level, if you don’t have succinct security requirements defined, then it’s really hard to verify or check something in the design. What often happens is customers will say, ‘I want to have a secure chip.’ But it’s not as easy as just pressing a button and getting a green check mark that confirms the chip is now secure.”
To be successful, engineering teams must start at the architectural stages and define the security requirements. “Once that is done, they can start actually writing the RTL,” Oberg said. “There are tools available to provide assurances these security requirements are being met, and run within the existing simulation and emulation environments to help validate the security requirements, and help identify any unknown design weaknesses. Generally, this helps hardware and verification engineers increase their productivity and build confidence that the system is indeed meeting the security requirements.”
![]()
Fig. 1: A cybersecurity model includes multiple stages, progressing from the very basic to in-depth. It is important for organizations to know what stages their cyber defense system are. Source: Cycuity
Steve Garrison, senior vice president, marketing of Stellar Cyber, noted that if cyber threats were uncovered during the detection process, so many data files may be generated that they will be difficult for humans to sort through. Graphical displays can speed up the process and reduce the overall mean time to detection (MTTD) and mean time to response (MTTR).
![]()
Fig. 2: Using graphical displays would reduce the overall meantime to detection (MTTD) and meantime to response (MTTR). Source: Stellar Cyber
Testing is essential
Another important stage in the design process is testing, whereby each system design requires a vigorous attack simulation tool to weed out the basic oversights to ensure it meets the predefined standard.
“First, if you want to understand how defensive systems will function in the real world, it’s important to test them under conditions, which are as realistic as possible,” Keysight’s Register said. “The network environment should have the same amount of traffic, mix of applications, speeds, behavioral characteristics, and timing as the real world. For example, the timing of a sudden uptick in email and social media traffic corresponds to the time when people open up their laptops at work. The attack traffic needs to be as realistic as possible as well – hackers try hard not to be noticed, often preferring ‘low and slow’ attacks, which may take hours or days to complete, making detection much more difficult. The same obfuscation techniques, encryption, and decoy traffic employed by threat actors needs to be simulated as accurately as possible.”
Further, due to mistaken assumptions during testing, defensive systems often perform great in the lab, yet fail spectacularly in production networks. “Afterwards we hear, for example, ‘I didn’t think hackers would encrypt their malware,’ or ‘Internal e-mails weren’t checked for malicious attachments, only those from external senders,’” Register explained. “Also, in security testing, currency is key. Attacks and obfuscation techniques are constantly evolving. If a security system is tested against stale attacks, then the value of that testing is limited. The offensive tools should be kept as up to date as possible to ensure the most effective performance against the tools a system is likely to encounter in the wild.”
Semiconductor security
Almost all system designs depend on semiconductors, so it is important to ensure that any and all chips, firmware, FPGAs, and SoCs are secure – including those that perform ML functionality.
“Semiconductor security is a constantly evolving problem and requires an adaptable solution, said Jayson Bethurem, vice president marketing and business development at Flex Logix. “Fixed solutions with current cryptography that are implemented today will inevitably be challenged in the future. Hackers today have more time, resources, training, and motivation to disrupt technology. With technology increasing in every facet of our lives, defending against this presents a real challenge. We also have to consider upcoming threats, namely quantum computing.”
Many predict that quantum computing will be able to crack current cryptography solutions in the next few years. “Fortunately, semiconductor manufacturers have solutions that can enable cryptography agility, which can dynamically adapt to evolving threats,” Bethurem said. “This includes both updating hardware accelerated cryptography algorithms and obfuscating them, an approach that increases root of trust and protects valuable IP secrets. Advanced solutions like these also involve devices randomly creating their own encryption keys, making it harder for algorithms to crack encryption codes.”
Advances in AI/ML algorithms can adapt to new threats and reduce latency of algorithm updates from manufacturers. This is particularly useful with reconfigurable eFPGA IP, which can be implemented into any semiconductor device to thwart all current and future threats and optimized to run AI/ML-based cryptography solutions. The result is a combination of high-performance processing, scalability, and low-latency attack response.
Chips that support AI/ML algorithms need not only computing power, but also accelerators for those algorithms. In addition, all of this needs to happen without exceeding a tight power budget.
“More AI/ML systems run at tiny edges rather than at the core,” said Detlef Houdeau, senior director of design system architecture at Infineon Technologies. “AI/ML systems don’t need any bigger computer and/or cloud. For instance, a Raspberry Pi for a robot in production can have more than 3 AI/ML algorithms working in parallel. A smartphone has more than 10 AI/ML functions in the phone, and downloading new apps brings new AI/ML algorithms into the device. A pacemaker can have 2 AI/ML algorithms. Security chips, meanwhile, need a security architecture as well as accelerators for encryption. Combining an AI/ML accelerator with an encryption accelerator in the same chip could increase the performance in microcontroller units, and at the same time foster more security at the edge. The next generation of microelectronics could show this combination.”
After developers have gone through design reviews and the systems have run vigorous tests, it helps to have third-party certification and/or credentials to ensure the systems are indeed secure from a third-party independent viewpoint.
“As AI, and recently generative AI, continue to transform all markets, there will be new attack vectors to mitigate against,” said Arm’s Maidment. “We expect to see networks become smarter in the way they monitor traffic and behaviors. The use of AI/ML allows network-based monitoring at scale to allow potential unexpected or rogue behavior to be identified and isolated. Automating network monitoring based on AI/ML will allow an extra layer of defense as networks scale out and establish effectively a ‘zero trust’ approach. With this approach, analysis at scale can be tuned to look at particular threat vectors depending on the use case.”
With an increase in AI/ML adoption at the edge, a lot of this is taking place on the CPU. “Whether it is handling workloads in their entirety, or in combination with a co-processor like a GPU or NPU, how applications are deployed across the compute resources needs to be secure and managed centrally within the edge AI/ML device,” Maidment said. “Building edge AI/ML devices based on a hardware root of trust is essential. It is critical to have privileged access control of what code is allowed to run where using a trusted memory management architecture. Arm continually invests in security, and the Armv9 architecture offers a number of new security features. Alongside architecture improvements, we continue to work in partnership with the industry on our ecosystem security framework and certification scheme, PSA Certified, which is based on a certified hardware RoT. This hardware base helps to improve the security of systems and fulfill the consumer expectation that as devices scale, they remain secure.”
Outlook
It is important to understand that threat actors will continue to evolve attacks using AI/ML. Experts suggest that to counter such attacks, organizations, institutions, and government agencies will have to continually improve defense strategies and capabilities, including AI/ML deployment.
AI/ML can be used as weapon from an attacker for industrial espionage and/or industrial sabotage, and stopping incursions will require a broad range of cyberattack prevention and detection tools, including AI/ML functionality for anomaly detection. But in general, hackers are almost always one step ahead.
According to Register, “the recurring cycle is: 1) hackers come out with a new tool or technology that lets them attack systems or evade detection more effectively; 2) those attacks cause enough economic damage that the industry responds and develops effective countermeasures; 3) the no-longer-new hacker tools are still employed effectively, but against targets that haven’t bothered to update their defenses; 4) hackers develop new offensive tools that are effective against the defensive techniques of high-value targets, and the cycle starts anew.”
Related Reading
Securing Chip Manufacturing Against Growing Cyber Threats
Suppliers are the number one risk, but reducing attacks requires industry-wide collaboration.
Data Center Security Issues Widen
The number and breadth of hardware targets is increasing, but older attack vectors are not going away. Hackers are becoming more sophisticated, and they have a big advantage.
The post Using AI/ML To Combat Cyberattacks appeared first on Semiconductor Engineering.
-
Gamepur

-
Anime World Tower Defense (AWTD) Codes (June 2024)
Updated: June 24, 2024 We searched for the latest codes! There is no better way to dive into a Roblox game than with your favorite anime heroes. In Anime World Tower Defense, your mission is to stop the evil army of the Corrupted Hero from reaching your base and make everything wrong in this universe right again! Some battles will be more challenging than others, so try to use Anime World Tower Defense codes for essential resources such as Puzzles, Gold, Candy, and Miracle Shards to
Anime World Tower Defense (AWTD) Codes (June 2024)
Updated: June 24, 2024
We searched for the latest codes!
There is no better way to dive into a Roblox game than with your favorite anime heroes. In Anime World Tower Defense, your mission is to stop the evil army of the Corrupted Hero from reaching your base and make everything wrong in this universe right again!
Some battles will be more challenging than others, so try to use Anime World Tower Defense codes for essential resources such as Puzzles, Gold, Candy, and Miracle Shards to upgrade your Units and unleash the biggest power ever seen! In the meantime, if you want to test your skills in a similar game with a lot of freebies, visit our Tower Defense X codes list.
All Anime World Tower Defense Codes List
Anime World Tower Defense Codes (Working)
- MusclePower — Unlocks 3K Puzzles and 50 Reroll Tokens (New)
- PhantomLeaderWhere — Unlocks 5450 Puzzles and 55 Reroll Tokens (New)
- 150kFav — Unlocks 15k Puzzles, 3 Miracle Shards, and 150 Reroll Tokens (New)
- 125MVisit — Unlocks 12.5k Puzzles, 3 Miracle Shards, and 125 Reroll Tokens (New) (Requires level 50+)
- SwordMaster — Unlocks 3k Puzzles and 25 Reroll Tokens
- MicaaPeemSoReal — Unlocks 10k Puzzles, 5 Miracle Shards, and 10 Cursed Dolls
- DragonKingdom — Unlocks 3k Puzzles and 25 Reroll Tokens
- Ninetails — Unlocks 3k Puzzle and 25 Reroll Tokens
- 1MGolds — Unlocks 1 million Gold
- 100MVisit — Unlocks 10k Puzzles, 5 Miracle Shards, and an Exclusive Skin (Requires level 50+)
- GodShinobi — Unlocks 3k Puzzle
- SorryForQuestBug — Unlocks 5k Puzzles and 1 Miracle Shards
- 30KLikesTysm — Unlocks Puzzles (New servers only)
- UchigoDaigan — Unlocks 3k Puzzles
- 75MVisit — Unlocks 3k Puzzles and 750k Gold (Requires level 25+)
- 125KFav — Unlocks 10k Puzzles and 5k Spirits (Requires level 25+)
- MerryChristmasAWTD2023 — Unlocks 10k Christmas Bells and a Legendary Padoru Unit
- CHRISTMAS2023 — Unlocks 3k Christmas Bells
Anime World Tower Defense Codes (Expired)
Related: Circus Tower Defense Codes
How to Redeem Codes in Anime World Tower Defense
Redeeming codes in Anime World Tower Defense is a simple process. Follow our instructions to claim your rewards right away:

- Launch Anime World Tower Defense on Roblox.
- Click on the Settings button on the left side of the screen.
- Scroll to the bottom of the pop-up window and enter the code in the text box.
- Hit Enter to grab your free rewards.
How Can You Get More Anime World Tower Defense Codes?
The easiest way to get the latest Anime World Tower Defense codes is to bookmark this article (CTRL+D) and check back occasionally, as we do everything we can to find all the active ones and put them here, in one place, to spare you that tiresome procedure.
On the other hand, if you want to search for them on your own, you can check the developer’s official social media channels:
Why Are My Anime World Tower Defense Codes Not Working?
Watch out while entering AWTD codes because they’re usually made from upper- and lower-case letters, so typos can happen in the blink of an eye. We suggest copying the code you want to use from our Working list and pasting it straight into the game to avoid mistakes.
Also, if you get the message Code Invalid, that means the code has most likely expired, so redeem all of them as soon as you see the ones you have yet to use. If you run into an inactive code, even if it’s on our active list, let us know, and we will investigate the issue.
What Is the Anime World Tower Defense Trello Link?
If you want an advantage over your opponents before every battle, use the AWTD Trello board. It’s free to access and full of information about the game that can be a great asset during your experience. Everything is there — from Unit mechanics and maps to enemy types and numerous tips and tricks on defeating the Corrupted Hero. Use it whenever you run into problems during the most challenging clashes.
What Is Anime World Tower Defense?
AWTD is a tower-defense game on Roblox where you must stop the Corrupted Hero’s army from destroying your base by placing Units that are actually your favorite anime heroes. Enemies are coming your way fast and in waves, so you have to level up your game more than in any other title from this genre. Summon your heroes with Puzzles and try to endure as much as possible in every round if you want to reach the top of the leaderboard.
If you play more Roblox games with the code redemption feature, make sure to visit our dedicated Roblox Codes section and get all the goodies in other popular titles.
-
Gamepur

-
Skibi Defense Codes 3.5 (August 2024)
Updated: August 6, 2024 We looked for new codes! Skibi Defense is a game that will make you dance to epic battle music while watching your enemies get destroyed by your powerful units. I managed to clear 11 waves and defeat mighty foes like the Balloon Toilet. However, I did have some help. You will have to grind a lot for rewards in this game, but luckily, Skibi Defense codes are here to assist you! Redeem them to get free extra Credits to upgrade or buy new units and Boosts to doub
Skibi Defense Codes 3.5 (August 2024)
Updated: August 6, 2024
We looked for new codes!
Skibi Defense is a game that will make you dance to epic battle music while watching your enemies get destroyed by your powerful units. I managed to clear 11 waves and defeat mighty foes like the Balloon Toilet. However, I did have some help.
You will have to grind a lot for rewards in this game, but luckily, Skibi Defense codes are here to assist you! Redeem them to get free extra Credits to upgrade or buy new units and Boosts to double the rewards you’ll get while clearing waves. You can also get crates with random gifts for free by redeeming the codes listed below! If you want more tower defense fun, check out our Tower Defense X Codes article to get more codes and claim amazing rewards in that game, too!
All Skibi Defense Codes List
Active Skibi Defense Codes
- datafixed: Unlocks 1h of 2x and 3x boost and 5k Credits (New)
- wowdelaycrazy: Unlocks 2k Shards (New)
- 200milvisits: Unlocks 1h 3x boost (New)
- update3in0: Unlocks 1h 3x boost (New servers only)
- 10kfollowers: Unlocks free rewards (New servers only)
- needmorefollowers: Unlocks 1h 3x boost
- massping: Unlocks 1h 3x boost
- stpatricks: Unlocks 1h 3x boost
- updatein0: Unlocks 4k Credits
- 100klikes: Unlocks 3.5k Credits
- sorryfordelays: Unlocks rewards
- fixedboost: Unlocks 1 hour of 3x boost
- 30kagain: Unlocks 1 hour of 3x boost
- 20kcomeback: Unlocks 10,000 Credits
- consistentupdates: Unlocks 3,000 Credits
- early100mil: Unlocks 5,000 Credits and 2x boost
- happyvalentines: Unlocks 1 hour of 2x boost and 2,750 Credits
- thxfor100kmembers: Unlocks 1,500 Credits and 3x boost for 30 minutes
- 50MVisits: Unlocks 2h 2x boost, 30 minutes 3x boost and 2,500 Credits
- sorryforshutdowns: Unlocks 3h of 2x boost and 3,000 Credits
- UPD2: Unlocks 3x Credit Boost
- 25mvisits: Unlocks Credits
- 50klikes: Unlocks Credits
- 20kplayers: Unlocks Credits
- 25klikes: Unlocks 2x Boost Case
- 10kplayers: Unlocks 3x Boost Case
- 10mvisits: Unlocks 2x Boost Case
- 2.5klikes: Unlocks Credits
- 5klikes: Unlocks Credits and Case
- 10kfavs: Unlocks Credits and Case
- 5kplayers: Unlocks Credits and Boost Case
Expired Skibi Defense Codes
Related: Skibi Toilet Tower Defense Codes
How to Redeem Codes in Skibi Defense
To redeem Skibi Defense codes, follow these instructions:

- Launch Skibi Defense in Roblox.
- Open the in-game chat.
- Type /redeem (code) into the text box.
- Press Enter and claim your goodies!
How Can You Get More Skibi Defense Codes?
Social media platforms are always a good place to check if you’re considering looking for Skibi Defense codes on your own. Become a Skibi Defense Discord server member and get the latest updates and scour for the newest code drops. Connect with other players by joining the official Archkos Studios Roblox group.
However, if you want to avoid a lot of unrelated messages on social media, our article is the best source to stay on top of the latest codes. By bookmarking this page, you’ll get all the newest codes and freebies for this game in one place.
Why Are My Skibi Defense Codes Not Working?
Compare the code you’ve just entered manually with the Skibi Defense codes on our list. Are they the same? If the answer is no, then a typo must have sneaked in. It’s crucial to keep an eye on details, as one slip-up can cause the entire code to go invalid. If you want to skip these problems altogether, the best option would be to copy and paste the code you want to use directly from our list into the text box.
If the spelling is fine, but you still have no luck with getting your freebies, the code you’re trying to use is probably no longer active. Despite our best efforts to keep our articles current, developers rarely disclose expiration dates for codes. So, if you find an expired code on our active list, contact us so we can assist with the issue and update our lists quickly.
Other Ways to Get Free Rewards in Skibi Defense
Crates are another way to get rewards once you run out of Skibi Defense codes to redeem. You can open one free crate daily or unlock more by completing quests. There are two types of crates to open: those for credits and for boosts. The selection of goodies is randomized, but you’ll see a list of all potential items you can get inside the chosen box.
What Is Skibi Defense?
Skibi Defense is a Roblox tower defense game inspired by the popular YouTube series called Skibidi Toilets. Like other tower defense titles, this is a strategy-based game with a hilarious twist of NPC characters designed as toilets or humans with cameras instead of heads. Your role is to place your camera units around the map in strategic positions to secure your base and watch as they destroy waves of opponents. There are several available gameplay modes — the primary Story mode, the Versus mode, and the Endless mode.
If you want to look around for more codes for your other Roblox games, skim through our Roblox Codes section to claim many exciting freebies fast!
-
GameSkinny

-
Roblox All Star Tower Defense Codes — ASTD (August 2024)
Updated: August 21, 2024 Checked for codes!The post Roblox All Star Tower Defense Codes — ASTD (August 2024) appeared first on GameSkinny.
Roblox All Star Tower Defense Codes — ASTD (August 2024)
Updated: August 21, 2024
Checked for codes!
The post Roblox All Star Tower Defense Codes — ASTD (August 2024) appeared first on GameSkinny.
